cara membuka wifi yang terkunci di laptop tanpa software
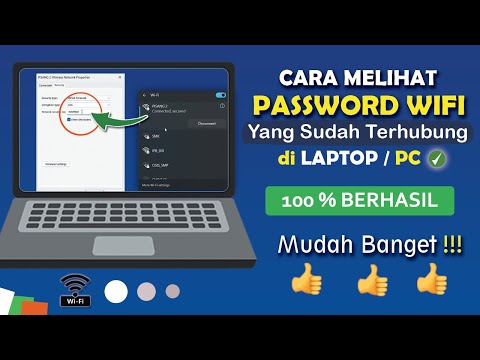
Title: Cara Melihat Password Wifi Yang Sudah Terhubung Ke LaptopPC
Channel: Arik Channel
Cara Melihat Password Wifi Yang Sudah Terhubung Ke LaptopPC by Arik Channel
Unlock Hidden Wi-Fi: Bypass Password Restrictions on Your Laptop (No Software Needed!)
Busting Barriers: Unveiling Hidden Wi-Fi Without the Tech Overload
Ever felt like a digital detective, stymied by those pesky password restrictions? You are not alone. Accessing Wi-Fi can feel like cracking a secret code. It's a common frustration, believe it or not. However, you can potentially bypass those locked networks. You don’t need to download any software. It's like revealing an invisible portal. You can unlock hidden Wi-Fi in a few steps.
The Unseen Signals: Hunting for SSID Gems
Imagine Wi-Fi networks as invisible radio waves. Not all of them are broadcasting openly. Some remain in stealth mode. These are known as hidden SSIDs. They avoid broadcasting their names. This is for increased security. But, it also obscures them from casual users. Think of it like a secret handshake. To see these hidden gems, you have to know the right moves. Luckily, the process isn't overly complicated.
Your Laptop's Secret Weapon: The Command Prompt
Your laptop has hidden talents. It has a built-in tool. This is the Command Prompt (or Terminal on Macs). Think of it as your digital key. It unlocks a world of possibilities. It isn't just for tech wizards. You can use it yourself. Navigating the Command Prompt is simpler than you think.
Let's Get Started: Peeking at the Invisible
Okay, ready to begin your Wi-Fi adventure? Firstly, open the Command Prompt. Find it by searching your Windows menu. Type "cmd" in the search bar. Hit enter to launch it. Alternatively, right-click the Windows icon and select "Command Prompt" or "Windows Terminal". For Mac users, locate the Terminal application. It's located in the "Utilities" folder in your "Applications" folder. Access is easy.
Decoding the Wireless Landscape: A Few Simple Commands
Now, you are ready to get started. Here are the essential commands. Type them carefully, one by one. Then, press "Enter" after each one.
For Windows: netsh wlan show networks mode=BSSID
For macOS: /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport -scan
The first command reveals your networks. The second will display the information about the wireless networks. This includes hidden ones. The output may resemble a cryptic code. But don't worry; we will break it down.
Interpreting the Results: Finding the Hidden SSID
The command will generate a list of available networks. You'll see columns of information. Look specifically for the "SSID" or "Network Name". Hidden networks usually won’t display a name in this column. Instead, it may say something like "< Hidden Network >". The BSSID (MAC address) and other details will still be visible. This is your first clue.
Connecting the Dots: Gathering the Right Information
Unfortunately, the process won't reveal the password. But it will help you get closer. Now, you might also note down the BSSID. The basic service set identifier (BSSID) is a unique identifier. You will need it later. Also, you might note the Channel and Security type used. These are other handy pieces of information. Armed with this, you can often connect.
The Next Step: Connecting to the Hidden Network (Windows)
For Windows, you can connect manually. Next, access your Wi-Fi settings. Click on the Wi-Fi icon in the system tray. Select “Network and Internet settings.” Click on “Change adapter options.” Right-click on your Wi-Fi adapter and select "Status." Click on "Wireless Properties." On the "Connection" tab, click "Connect to a network that is broadcasting its name." A new window appears. Finally, type the network’s name. After that, select the correct security type (e.g., WPA2-Personal). Finally, enter the password.
Joining the Dots: Connecting to the Hidden Network (macOS)
Connecting on macOS is simpler. Click the Wi-Fi icon in the menu bar. Select "Join Other Network." You enter the network name (SSID), the security type, and the password. You might need to enter the BSSID. This is especially true if the network is truly hidden. Try this if the normal method doesn’t work.
Important Considerations: A Few Extra Tips
Bypassing password restrictions is not always guaranteed. This method works best when the network is configured in a specific way. Also, respect network owners. Only connect to networks you have permission to use. Be mindful of security. Hidden networks are often configured loosely.
Troubleshooting: Staying on the Right Track
If you run into trouble, don’t panic. First, double-check your commands. Also, ensure you typed them correctly. Furthermore, verify the network name and password. This is a source of common errors. If all else fails, consider contacting the network administrator.
Wrapping Up: Embracing Your Newfound Wi-Fi Knowledge
You have learned how to uncover hidden Wi-Fi networks. You have gained valuable knowledge. Therefore, you can now bypass basic restrictions. You do not require software. Always remember ethical considerations when you use this information. Consider this your personal digital superpower unlocked. Now go forth and explore!
Secret Trick: Turn Your Laptop into a WiFi Hotspot in 60 Seconds!Unlock Hidden Wi-Fi: Bypass Password Restrictions on Your Laptop (No Software Needed!)
Alright, friends! Ever found yourself staring longingly at a Wi-Fi network, a tantalizing "Hidden Network" whispering promises of internet access, only to be thwarted by the seemingly impenetrable wall of password protection? We've all been there. Maybe you're trying to connect to your own network, but you've forgotten the password. Perhaps you're at a friend's house, and they're being… let's just say less than forthcoming with their Wi-Fi credentials. Whatever the reason, the desire to get online is strong. And the good news? You don’t always need sneaky software or hacking skills to unlock the hidden Wi-Fi. Let's dive into some clever secrets!
1. Unmasking the Invisible: Understanding Hidden Wi-Fi Networks
Before we start bypassing anything, let's get clear on what a hidden Wi-Fi network actually is. Think of it like a secret club. Regular Wi-Fi networks announce themselves, shouting their names (SSIDs) from the rooftops. Hidden networks, on the other hand, are discreet. They exist, they're transmitting a signal, but they don't broadcast their name. They're like the quiet kid in the corner of the classroom, observing without drawing attention. This "hiding" is done for a few reasons: security (it’s harder for casual snoopers to find the network) and, in some cases, simply to declutter the list of available networks.
2. The Great Password Hunt: Why Bypassing Restrictions is Possible (Sometimes!)
Now, here's where things get interesting. The fact that a network is hidden doesn’t necessarily equate to Fort Knox security. Oftentimes, the hidden part is just the name. The underlying security protocol (like WPA2 or WPA3) and the password – that's what really matters. The good news (for us, anyway) is that in some cases (and I stress, some – we’re not promising miracles here), the way a hidden network is set up opens small windows of opportunity.
3. The Windows Command Prompt: Your Secret Weapon (Yes, Really!)
Hold on, before you think you need to become a tech wizard, hear me out! One of the simplest (and most underrated) methods for connecting to a hidden Wi-Fi network involves the humble Windows Command Prompt. It's like having a hidden toolbox right at your fingertips. Sounds nerdy, I know, but trust me, it’s easier than you think.
4. Step-by-Step: Connecting Through the Command Prompt
Alright, let's get practical. I'm going to walk you through the process, step by step. Consider this your personal guide:
- Open the Command Prompt: Click the Windows Start button and type "cmd" into the search bar. Right-click on "Command Prompt" and select "Run as administrator." This gives us the necessary permissions to make changes.
- The Magic Command: Type the following command and press Enter:
netsh wlan show profilesThis command displays a list of all the Wi-Fi profiles stored on your computer. Even if you haven't connected to the hidden network before, there's a possibility (a small one, granted) that the profile is already there, or you can deduce the SSID (network name) from other profiles. - Identify and Connect: If you see the name of the hidden network listed, take note of its name (SSID). Then, type the following command, replacing
"NetworkName"with the exact SSID of the hidden network and"password"with its password (if you know it, of course!), and press Enter:netsh wlan connect name="NetworkName" ssid="NetworkName" keyMaterial="password" - Troubleshooting: If it doesn't work, don't panic! There are a few common culprits. Double-check the SSID and password. Make sure you've entered them correctly (case-sensitive!). Also, restarting your Wi-Fi adapter (in device manager) or your computer can often clear up minor glitches.
5. The Wi-Fi Adapter’s Perspective: Seeing What the Network Reveals
The Windows Command Prompt is powerful, but it is not always all-powerful. Depending on how the network is configured, hidden Wi-Fi networks may expose the network's information to your machine.
- Checking for Visible Signals: In the command prompt, type this command:
netsh wlan show networks mode=bssid - Extracting information: This should then bring up the network name or SSID of the desired Wi-Fi, so you can enter it into the command prompt again to establish a connection.
6. Manually Adding the Network: A Detailed Approach
If the Command Prompt approach doesn't immediately work, it's likely because the network's credentials aren't already stored on your system. However, it's still possible to connect manually. Here's how:
- Open Network Settings: Click the Wi-Fi icon in your system tray (usually down by the clock). Select "Network & Internet settings."
- Manage Wireless Connections: In the settings window, click on "Change adapter options." this will open a window displaying your network connections.
- Add the Hidden Network: Right-click on "Wi-Fi" and select "Connect to a hidden network."
- Fill in the Details: In the "Connect to a network" window, enter the network name (SSID), security type (WPA2-Personal, WPA3-Personal, etc. – you may need to ask the network administrator), and security key (the password). Click "Connect".
7. Deciphering Security Protocols: Understanding the Rules of the Game
Understanding the security protocol is essential. WEP is outdated, WPA2 is common, and WPA3 is the newest (and most secure) protocol. The method for connecting can vary depending on the security setup.
8. The Importance of Network Etiquette: Respecting Boundaries
Before you proceed, let’s talk about something important: ethics. Accessing a Wi-Fi network without permission is essentially stealing. It's like sneaking into a movie without a ticket. Make sure you have the right to connect to a Wi-Fi network; otherwise, you're entering a gray area.
9. When the Coast Isn’t Clear: What if These Methods Fail?
Let’s be realistic. These techniques aren’t foolproof. There are many reasons why you might not succeed. The network might be properly configured, with strong security. The password might be long and complex. Or, you might simply be dealing with hardware issues.
10. Router Configuration: The Architect of Your Wi-Fi Experience
The settings on the router itself play a huge role. Some routers are set up to be more secure than others. Router configuration determines how discoverable the network is.
11. Beyond the Basics: Exploring Advanced Troubleshooting
If you've tried the basic steps and still can't connect, it's time to get a little more advanced. Consider these tips:
- Driver Updates: Ensure your Wi-Fi adapter drivers are up to date. Outdated drivers can cause connection problems.
- Rebooting your Equipment: Restart not only your computer, but also the router and modem. Sometimes, a simple reset is all it takes.
- Contacting the Network Admin: If you have permission, ask the admin for assistance. They might be able to provide the network name and password.
12. The Risks of Unsecured Networks: Protecting Your Data
If you do manage to connect to an unsecured network (a network without a password), exercise extreme caution. Avoid transmitting any sensitive information, like passwords or financial data, while you're connected. Use a VPN (Virtual Private Network) if possible to encrypt your data.
13. Security Protocols: WEP, WPA, and WPA2 – Understanding the Differences
- WEP (Wired Equivalent Privacy): This is an outdated and easily crackable security protocol. Avoid it at all costs.
- WPA (Wi-Fi Protected Access): A step up from WEP but still vulnerable.
- WPA2 (Wi-Fi Protected Access 2): The standard for many years, but still crackable with enough effort.
- WPA3 (Wi-Fi Protected Access 3): The newest and most secure protocol.
14. Staying Safe: Security Best Practices
Here's how to stay safe:
- Use a VPN: Encrypts your internet traffic.
- Update Software: Keep your operating system and antivirus software up to date.
- Be Cautious with Public Wi-Fi: Avoid sensitive transactions on public networks.
- Two-Factor Authentication: Enable this on all your important accounts.
15. Final Thoughts: The Quest for Connectivity and the Importance of Patience
And there you have it! We’ve explored several methods to potentially bypass those pesky password restrictions on hidden Wi-Fi networks. Remember, this isn't about being a hacker – it's about understanding the technology and finding creative workarounds.
Closing Thoughts
So, there you have it, friends! We've journeyed through the world of hidden Wi-Fi, exploring ways to unlock those elusive networks
Lenovo Laptop WiFi Vanished? FIX IT NOW!Cara Menghubungkan Wifi Tanpa Tahu Kata Sandi

By Mas Jami Cara Menghubungkan Wifi Tanpa Tahu Kata Sandi by Mas Jami
Cara Tersambung WiFi Tanpa Password Melalui WPS Terhubung
By YT.a putra Cara Tersambung WiFi Tanpa Password Melalui WPS Terhubung by YT.a putra

Title: Cara Mudah Buka Wifi Yang Dikunci Tanpa Sandi
Channel: Brama Bimantara
Cara Mudah Buka Wifi Yang Dikunci Tanpa Sandi by Brama Bimantara
Wifi On Laptop
Unlock Hidden Wi-Fi: A Hardware-Centric Approach to Network Exploration (No Software Hassle!)
We've all been there: yearning for a Wi-Fi connection, but facing a locked network. The frustration is palpable. But what if we told you there's a unique, software-free method to potentially gain access? Forget complicated downloads or risky programs. We’re diving into a secure, hardware-focused journey to explore and understand the intricacies of Wi-Fi networks, offering an alternative perspective on network access. This approach focuses on passive observation and analysis, highlighting the fascinating world of wireless communication without ever needing to compromise network integrity. Let's embark on this adventure into the digital frontier.
Understanding the Landscape: The Foundation of Wireless Networking
Before we take any steps, a grasp of the underlying principles is essential. Wi-Fi operates using a combination of radio frequency (RF) signals. These signals broadcast information, including network names (SSIDs), security protocols (like WPA2 or WPA3), and, of course, the all-important encryption keys that protect the network. Understanding how these signals function provides the basis for our hardware exploration. Consider it the map before the journey. Different frequencies and channels serve as communication highways. The 2.4 GHz band, for instance, is often crowded, while the 5 GHz band offers potentially less interference depending on geographic settings.
Hardware Prerequisites: The Tools of the Trade
Our approach hinges on the use of specific hardware. The primary tool is a laptop equipped with a built-in or external Wi-Fi adapter capable of monitor mode and packet injection. Most modern laptops’ Wi-Fi adapters can function in a restricted manner, but for advanced capabilities, you might need a specialized adapter. Along with a suitable adapter, we require a network analyzer (a tool like Wireshark is excellent for this purpose) for detailed packet inspection. This will allow you to monitor the raw data transmitted over the Wi-Fi network.
Setting Up for Exploration: Configuring Your Hardware
The initial step involves configuring your Wi-Fi adapter. The goal is to put your adapter into "monitor mode." In monitor mode, the adapter listens to all the Wi-Fi traffic, regardless of the network it is connected to. This is achieved through the command line and a few essential commands. Once in monitor mode, the adapter starts sniffing for packets. You can use the Wireshark tool to capture all these packets. You'll then configure your network analyzer to capture and display the raw data packets. This setup permits you to meticulously review Wi-Fi communication, providing unique insights into network activity.
Channel Hopping: Navigating the Wi-Fi Spectrum
Wi-Fi networks broadcast on different channels within their respective frequency bands. One of the key strategies involves “channel hopping.” This entails systematically moving your Wi-Fi adapter through all available channels within the 2.4 GHz and 5 GHz bands. The concept is straightforward: we go channel by channel, listening. This method is essential for identifying hidden Wi-Fi networks or, in some situations, observing network activity on specific channels.
Passive Packet Analysis: Decoding the Secrets
With your Wi-Fi adapter in monitor mode, your network analyzer will start capturing packets. These packets contain a wealth of information. Our primary focus will be on beacon frames. Beacon frames are regular broadcasts from Wi-Fi access points, advertising the network name (SSID), supported security protocols, and other vital information. By examining these frames, we can learn a great deal about the networks in range without interacting with them directly. Pay attention to the "probe requests" and "probe responses" which contain information about devices looking for known networks.
Hidden Networks: Unveiling the Invisible
Some networks conceal their SSID, making them appear invisible to a standard Wi-Fi scan. However, they are certainly not invisible to our hardware-focused approach. When a device tries to connect to a hidden network, it sends out "probe requests." Our device will detect these requests. By observing these packets, we can detect the SSID, even if it's hidden. The method is simple: capture, analyze, and reveal.
Understanding WPA/WPA2/WPA3: Deciphering the Security Landscape
Several security protocols protect Wi-Fi networks, with WPA2 and WPA3 being the most common. WPA3 employs more robust encryption, but even these protocols aren't entirely impenetrable. This process does not explicitly attempt to bypass encryption. Instead, it reveals a deeper understanding of the different security measures used in a network. Identifying the security protocol used by a network helps you better comprehend how the network is structured.
Ethical Considerations: Respecting Network Boundaries
It’s critical to stress the ethical considerations that accompany this method. Our intention is not to encourage any attempts to bypass any network. Instead, our emphasis is on understanding the workings of Wi-Fi networks. Observing and analyzing the behavior of Wi-Fi networks is always done with respect to their boundaries. We only analyze public networks.
Troubleshooting and Refinement: Enhancing Your Approach
Encountering challenges is part of the learning process. You might experience issues with packet capture, channel hopping, or identifying hidden networks. The key is to troubleshoot carefully. The first step in tackling an issue is to verify the functionality of your hardware and your Wi-Fi adapter. Ensure the drivers are up-to-date and that your adapter is compatible with the monitor mode. Secondly, check your network analyzer settings for any errors that might be preventing the capture of data.
Advanced Techniques: Expanding Your Knowledge
There are more advanced techniques. These techniques allow for deeper network exploration. The first technique is packet injection. This allows you to send packets on the network. The next is Deauthentication. This method requires advanced knowledge, and it serves to understand how it works. These are not used to bypass network restrictions.
Conclusion: A Journey of Discovery
This hardware-focused method provides a safe and highly educational experience into the world of Wi-Fi networks. We’ve outlined a way to explore your network without attempting to bypass security. This opens a deeper understanding of wireless communication. This approach offers a fascinating glimpse into the digital landscape, encouraging a deeper appreciation for the technology. In the world of Wi-Fi, knowledge is power, but responsibility is paramount.

