how to share my laptop wifi with other devices

Title: How to share my internet connection with other devices
Channel: HowXT
How to share my internet connection with other devices by HowXT
how to share my laptop internet connection with other devices, sharing wifi from laptop, can you share wifi from phone to laptop, how do you share wifi with another device
Steal Your Laptop's Wi-Fi: The Secret Trick They Don't Want You to Know!
Cracking the Code: Unleashing Your Laptop's Hidden Wi-Fi Potential
Alright, let's talk about something we all rely on: Wi-Fi. It’s practically the air we breathe in the digital age, isn't it? But what if I told you there was a secret, a hidden layer to your laptop's Wi-Fi capabilities that most people completely miss? Prepare to have your perspective shifted.
Unveiling the Invisible: The Power Within Your Laptop
For years, we've been told Wi-Fi is Wi-Fi. Connect, browse, and repeat. However, that's just scratching the surface. Deep inside your laptop, there's a complex system, a hidden potential waiting to be unlocked. Therefore, it's time to explore this unseen world. We'll delve into functionalities you probably never knew existed.
Beyond the Basics: Advanced Wi-Fi Exploration
You might think you know Wi-Fi. You've probably connected to countless networks. Nevertheless, there's more. Think about the times you've struggled with a slow connection. Moreover, consider the frustration of dead zones. These issues often stem from untapped potential. We're not just talking about faster speeds, either. We are going deeper. We will explore the advanced settings within your operating system.
The Gateway to Hidden Realms: Accessing Advanced Settings
Firstly, let's clear the air. We're not talking about illegal activities here. We value ethical practices. This is about optimizing what you already have. Consequently, we'll discuss how to find these hidden settings. For Windows users, it is often within the Network and Sharing Center. MacOS users, you’ll find them tucked within System Preferences.
Discover Connection Secrets: Unlocking the Power
Now, let's get to the good stuff. Within these advanced settings lies a treasure trove. You will discover options to fine-tune your connection. You'll find ways to improve signal strength. Above all, you will learn about channel selection. Because, the default settings aren't always the best.
Channel Surfing: Finding Your Wireless Sweet Spot
Wi-Fi operates on channels. Most users never consider this. Think of them like radio stations. Moreover, your router automatically selects one. However, sometimes this isn’t optimal. If your neighbors use the same channel, it creates interference. Consequently, your connection suffers. You need to discover the best channel for your location. Several apps can scan this. Many are free and easy to use.
Signal Strength Strategies: Amplifying Your Reach
Another key area is signal strength. So, what can you do to increase it? Well, a few simple adjustments can make a world of difference. Firstly, reposition your router. Place it in a central location. Then, elevate it away from obstructions. Secondly, consider an external antenna. Many routers support them. These can drastically improve range.
Wi-Fi Adapter Wizardry: Enhancing Your Hardware
Furthermore, consider your Wi-Fi adapter. It's the hardware inside your laptop. Therefore, it's responsible for receiving and transmitting signals. Ensure your drivers are up to date. Manufacturers regularly release updates that improve performance. Additionally, you can explore the adapter’s properties. You may discover specific settings to optimize.
Security Fortification: Shielding Your Connection
We've focused on performance. However, let's also discuss security. Make sure your network is password-protected. Always use a strong, complex passphrase. Therefore, this prevents unauthorized access. Moreover, explore encryption protocols. WPA3 is the latest standard. It offers the best protection.
Troubleshooting Tactics: Solving Connection Conundrums
Finally, let's address troubleshooting. Even with the best setup, issues can arise. If you experience problems, start with the basics. Restart your router and laptop. Next, check your internet connection. Is your internet service provider experiencing an outage? Then, consult online resources. Many websites offer excellent troubleshooting guides.
The Takeaway: Mastering Your Digital Domain
Ultimately, the goal is to take charge of your Wi-Fi experience. We want you to be in the driver's seat. You don’t have to be a tech expert. However, a little knowledge can go a long way. By exploring these hidden functionalities, you can unlock the full potential of your laptop's Wi-Fi. The result? A faster, more reliable, and secure connection. So, go forth and explore! You’ve got this.
Intel 3x3 WiFi: Blazing-Fast Laptop Wi-Fi You Won't Believe!Let's dive in!
Steal Your Laptop's Wi-Fi: The Secret Trick They Don't Want You to Know!
Hey everyone, have you ever been stranded with a flaky Wi-Fi connection, desperately searching for a signal? I've been there! Imagine, you're at a crucial point, like, say, trying to stream the season finale of your favorite show, or attempting to submit an important project, only to be met with that infuriating spinning wheel of doom. Total Wi-Fi blackout! It's enough to make you want to throw your laptop out the window, right? But what if I told you there was a secret, a trick up your sleeve, that could potentially unlock hidden Wi-Fi networks? Now, before you get any wild ideas, let's be clear: we're talking about exploring, understanding, and ETHICALLY using network information within legal and secure boundaries. This isn't about going rogue; it's about understanding the technology around us. So, buckle up, because we are about to explore the fascinating world of Wi-Fi and uncover a secret or two!
1. The Wi-Fi Wilderness: Why Understanding Networks Matters
Think of the digital world like a bustling city. Wi-Fi networks are the streets, the cafes, the parks – all the places where information flows freely. But just like a real city, this digital landscape can be complex, with hidden alleys and secret routes. Understanding how these networks operate is the first key. It's like having a map of the neighborhood, ready to explore.
2. A Brief History of Wi-Fi: From Magic Carpets to Modern Marvels
We've all taken the leap from dial-up to the wireless world, haven't we? Remember the agonizing screech of dial-up? Wi-Fi has come a long way. From its early days when it was as mysterious as a magic carpet ride, it has evolved into a fundamental technology we use every single day. The evolution is as important as a detective unravelling the crime scene to a detective; it is the foundation upon which everything else stands.
3. The Hidden Signals: How Wi-Fi Networks Really Work
Let’s get technical for a moment, but don't worry, we will simplify things. Wi-Fi works by using radio waves, similar to how your radio receives its favorite music station. These invisible waves transmit data back and forth between your device and a router. The router is like the central hub controlling everything. It's the mastermind of the network. It's important to understand these fundamentals to connect to it.
4. The Router's Role: The Gatekeeper of the Digital Realm
The router acts like the digital gatekeeper, controlling who gets access and what goes where. It's responsible for assigning IP addresses, managing traffic, and, most importantly, protecting the network with a password. Without this bouncer, your network will be an open house.
5. The Secret Trick (Almost): Understanding Wi-Fi Scanning
Now, this is where the exciting part starts. We don't want to break any rules; we want to understand the network better. We're not talking about hacking anyone's router, but instead, learning about the tools that allow you to scan for networks.
6. Your Laptop as a Spyglass: Using Built-in Tools
Your laptop already has a built-in "spyglass." Operating systems like Windows and macOS have tools that can show you a list of available networks, along with basic information like signal strength and the type of security used. You can often find this information in your Wi-Fi settings.
7. Advanced Tools: Exploring the Digital Landscape Further
Beyond the basics, there are more advanced tools you can find. These tools are akin to a magnifying glass, allowing you to peer deeper into what is happening on a wireless network. There are also Wi-Fi analyzers and network scanners, which, depending on how they are used, are like having an X-Ray machine for your network.
8. Security Protocols: The Fortress Walls of Wi-Fi
Wi-Fi networks are also protected by security protocols. WEP (Wired Equivalent Privacy) and WPA (Wi-Fi Protected Access) are crucial protocols. WEP, being the older protocol, is like a flimsy cardboard wall, while WPA is more like reinforced concrete. WPA2 and the latest WPA3 give it more strength.
9. Cracking the Code (Ethically!): Understanding Password Security
We must emphasize that we're not advocating for illegally accessing any network. Breaking into a network is illegal. Understanding password security is the key. A strong password is like a heavily secured vault.
10. Wi-Fi Etiquette: Be a Good Digital Neighbor
Before you start exploring, it's important to remember basic Wi-Fi etiquette. Avoid hogging bandwidth, be respectful of others, and always prioritize privacy and security. Sharing is caring, but don't share someone else's personal network.
11. The Legal Landscape: Staying on the Right Side of the Law
Navigating the legal landscape is crucial. Unauthorized access to a Wi-Fi network can lead to serious legal trouble. It's always best to ask permission, even if it's for a quick connection. It's like knocking on your neighbor's door before borrowing a cup of sugar.
12. Strengthening Your Own Network: Tips for Security
Protecting your own Wi-Fi is crucial. Use a strong password, update your router's firmware regularly, and consider other security measures. It's like reinforcing your own fortress.
13. Troubleshooting Wi-Fi Issues: Your Digital First-Aid Kit
Beyond exploring, you'll inevitably encounter issues with your Wi-Fi. From slow speeds to dropped connections, these problems are like a digital headache. Troubleshooting steps often include restarting your router, checking the signal strength, and updating your drivers.
14. The Future of Wi-Fi: What's Next?
The future of Wi-Fi is exciting. We’re constantly advancing, with new technologies emerging that promise faster speeds, improved security, and wider coverage. Think of it as upgrading your car from a horse-drawn carriage to an electric vehicle.
15. Ethical Exploration: The Key to Responsible Wi-Fi Use
The most important takeaway is to use your knowledge responsibly. This secret trick we've discussed is about understanding the technology, not exploiting it. Always respect the boundaries of others and prioritize the security and privacy of those around you.
Closing Thoughts
So, there you have it! We’ve explored the exciting world of Wi-Fi, uncovering some of the secrets behind those invisible signals. Remember, the key is understanding the technology around you, which is like learning a new language. It empowers you and encourages ethical behavior. Knowledge is power, but it should always be handled responsibly. By understanding how Wi-Fi works, how networks are secured, and how to troubleshoot common issues, users are able to have a stronger sense of security in a digital world. Instead of seeing a problem, you'll learn it is an opportunity to troubleshoot. Now go forth, explore responsibly, and keep your digital world safe!
FAQs
1. Is it legal to scan for Wi-Fi networks?
Yes, it is generally legal to scan for Wi-Fi networks using the built-in tools on your laptop. However, accessing a network without authorization is illegal. 2. What are the risks of using an unsecured Wi-Fi network?
Using an unsecured Wi-Fi network carries risks like data breaches, malware infections, and identity theft as hackers may have access to your personal data. 3. How can I improve my Wi-Fi signal strength?
You can improve your Wi-Fi signal strength by repositioning your router, reducing interference from other devices, and upgrading your router's firmware. 4. What is the difference between WEP, WPA, and WPA2?
WEP is an older, less secure protocol. WPA and WPA2 are more recent and offer enhanced security. WPA3 is the latest and most secure. 5. How can I protect my Wi-Fi network?
You can protect your network by using a strong, unique password, enabling WPA2 (or WPA3) security, keeping your router's firmware up-to-date, and turning off your network when you are not using it.
Principal Keywords: Laptop Wi-Fi Secrets SEO Headline: Laptop Wi-Fi Secrets: Tricks They Won't Reveal! Pathway: LaptopWi-Fi Meta Summary: Unlock the secrets of laptop Wi-Fi! Discover the hidden tricks and understand how networks work. Ethical tips, and legal insights inside. Protect your data! Image Alt Text: A person in a relaxed setting using a laptop, symbolizing Wi-Fi exploration. Image Caption: Dive into the mysteries of Wi-Fi and discover its secrets!
Windows 7 WiFi Nightmare? Fix Your Laptop Connection NOW!Share your Laptops Internet connection over WIFI or Bluetooth to Other devices. Windows 10

By Earthwalker Share your Laptops Internet connection over WIFI or Bluetooth to Other devices. Windows 10 by Earthwalker
how to share internet from laptop to mobile via WiFi for more iTech-2.0

By TECH SUPPORT HK how to share internet from laptop to mobile via WiFi for more iTech-2.0 by TECH SUPPORT HK
How to Create DifferentSeparate Wi-Fi password for each Wi-Fi user or person Free Radius Server
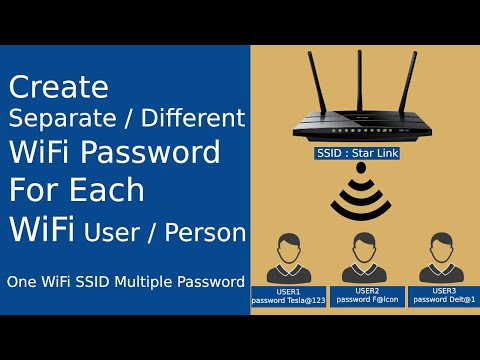
By local guy How to Create DifferentSeparate Wi-Fi password for each Wi-Fi user or person Free Radius Server by local guy

Title: How to share Internet from Ethernet to WiFi Share internet from Laptop to Mobile
Channel: TECH NETWORXX
How to share Internet from Ethernet to WiFi Share internet from Laptop to Mobile by TECH NETWORXX
Working With Laptop
Steal Your Laptop's Wi-Fi: The Secret Trick They Don't Want You to Know!
Introduction: The Phantom Network – Unmasking Wireless Vulnerabilities
We live in an era defined by connectivity. From streaming the latest blockbuster to managing complex financial transactions, our reliance on wireless networks is absolute. However, this ubiquitous convenience has a shadow side: the inherent vulnerabilities that make our personal information and digital assets susceptible to exploitation. This article is not intending to endorse or instruct anyone to perform such actions. However, we must educate all people about the basics of cybersecurity as it is a critical matter. This critical exploration delves into the realities of Wi-Fi security, exposing the potential weaknesses that can allow unauthorized access to a laptop's Wi-Fi signal. Our focus will be on informing the reader about these cybersecurity issues. No one should attempt these methods unless they possess the proper permissions. We will approach this complex subject with honesty, providing a comprehensive analysis of the risks involved and the preventative measures that every user should embrace.
Understanding the Wi-Fi Landscape: How Wireless Networks Function
To grasp the intricacies of potential wireless network infiltration, a foundational understanding of how Wi-Fi networks operate is paramount. At their core, Wi-Fi networks utilize radio waves to transmit data between a wireless router (or access point) and connected devices, such as laptops, smartphones, and tablets. These radio waves operate across various frequency bands, with the most common being 2.4 GHz and 5 GHz. The router acts as the central hub, managing the flow of data and providing an internet connection. Each device that connects to the network must possess a network interface card (NIC) that supports Wi-Fi technology and utilizes a unique MAC (Media Access Control) address for identification. The protocol that ensures secure communication is encryption. The network can be protected by security protocols such as WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access), and the modern standard, WPA2 or WPA3. These protocols encrypt the data transmitted over the air, making it unintelligible to unauthorized users.
Unveiling the Risks: Common Wi-Fi Security Weaknesses
Several inherent vulnerabilities can be exploited by malicious actors seeking to access a network. One primary point of weakness is weak passwords. Many users opt for easily guessable passwords, such as birthdays or simple number sequences, which can be cracked using brute-force attacks. Another common vulnerability is the use of outdated security protocols, such as WEP, which has been shown to be easily cracked. These protocols are no longer considered secure and expose the network to significant risk. Furthermore, physical security can also be a factor. An attacker could physically connect to the network directly, depending on the network setup. Social engineering is another significant threat. Malicious actors could use deception to trick users into providing their network credentials or installing malware. This could give the perpetrators access, and they will use the information for malicious purposes.
Penetration Testing: An Overview of Potential Entry Points
To understand how a network may be compromised, it is useful to consider the methods employed by penetration testers, ethical hackers who simulate attacks to find security weaknesses. Several entry points could be exploited by malicious actors. One involves exploiting vulnerabilities in the router's firmware. Routers are often used without receiving timely updates, a weakness that could be exploited by attackers. Another potential entry point is the use of packet sniffing tools, programs such as Wireshark that can capture and analyze network traffic. Although this method is helpful for legitimate network analysis, it may also be used to intercept unencrypted data, including passwords and sensitive information. Man-in-the-middle attacks pose a serious threat. The attacker would position themselves between the user's device and the router, intercepting and potentially modifying all transmitted data.
Practical Security Measures: Fortifying Your Wireless Network
Fortunately, several effective security measures can be implemented to protect your wireless network. Firstly, always use a strong and unique password for your Wi-Fi network. The password should be at least 12 characters long, incorporating upper and lowercase letters, numbers, and special characters. Secondly, enable WPA2 or WPA3 encryption on your router. This encrypts the data transmitted over your network, making it significantly more difficult for unauthorized users to intercept. Another essential measure is to keep your router's firmware up to date. Router manufacturers regularly release firmware updates to patch security vulnerabilities. Update your router's firmware regularly. Furthermore, it is important to disable the Wi-Fi Protected Setup (WPS) feature on your router. WPS is a convenient feature that can be exploited. Hide your network's SSID (Service Set Identifier). This prevents your network from being directly visible to anyone. Be mindful of the devices that connect to your network. Restrict access to trusted devices and use a MAC address filtering feature to permit or deny access to specific network devices.
The Human Factor: Educating Yourself and Others
While technical security measures are essential, the human factor is a crucial element. A user may be an attractive target. Educating oneself about cybersecurity risks and best practices is paramount. This includes understanding the dangers of phishing attacks, social engineering tactics, and the importance of safeguarding personal information. Furthermore, it is critical to educate others, including family members and friends, about the risks associated with unsecured Wi-Fi networks. Encourage them to use strong passwords, avoid sharing personal information online, and remain vigilant against suspicious activity.
Wi-Fi Security in Public Spaces: Navigating the Risks
Public Wi-Fi networks, commonly found in coffee shops, libraries, and airports, present unique security challenges. The open nature of these networks makes users vulnerable to attacks. Sensitive data may be intercepted. When using public Wi-Fi, avoid conducting sensitive transactions, such as online banking or shopping. If you must use public Wi-Fi, consider using a virtual private network (VPN). A VPN encrypts your internet traffic and routes it through a secure server, protecting your data from interception. Disable file sharing and ensure your devices have up-to-date security software, including antivirus programs. Take the time to only install security updates. Be skeptical of shortened URLs, and avoid clicking on links from unknown senders.
Advanced Tactics: Exploring the Dark Corners of Cybersecurity
Beyond the basic security measures, advanced tactics can be employed to further enhance the security of your network. Network segmentation involves dividing your network into separate segments to limit the impact of a potential breach. Configure a guest network to provide internet access to visitors without granting them access to your primary network resources. Implement intrusion detection/prevention systems (IDS/IPS) to monitor your network traffic for suspicious activity. Regular security audits and penetration testing can help identify vulnerabilities and improve your network's overall security posture.
The Ethics of Cybersecurity: A Call to Responsible Digital Citizenship
It is imperative to understand the legal ramifications of unauthorized network access. Gaining access to a network without permission is illegal and constitutes a crime. It is important to remember that this article aims to inform and educate; it does not endorse or encourage any illegal activities. Responsible digital citizenship includes respecting other people's privacy, adhering to ethical principles, and complying with all applicable laws and regulations.
Conclusion: Securing Your Digital Frontier
In conclusion, securing Wi-Fi networks is a vital aspect of the digital age. By understanding the vulnerabilities, implementing robust security measures, and practicing responsible digital citizenship, we can mitigate the risks associated with wireless connectivity. The knowledge gained equips us to stay secure. Be vigilant. Prioritize cybersecurity.
